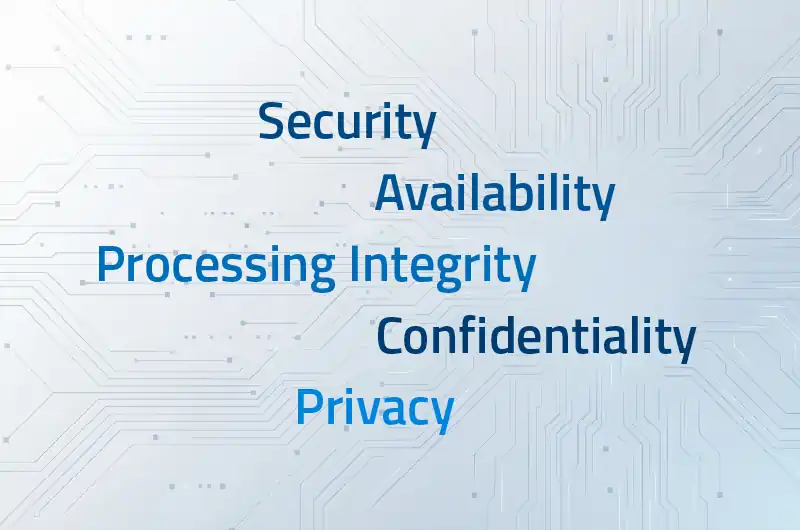
What Dangers Does SOC 2 Type 2 Actually Defend Against?
Think of SOC 2 Type 2 as your Fellowship standing guard against today’s digital threats:
|
Data Breaches & Unauthorized Access
The cyber equivalent of orcs breaking through the walls of Minas Tirith.
|
System Downtime
When your systems go dark like the beacons of Gondor failing to light. Customers can’t use what they can’t access.
|
Chaotic Internal Processes
Poor change management spreading corruption faster than Saruman’s influence.
|
Weak Confidentiality & Data Integrity
Like leaving the Ring unguarded, even the smallest gap can lead to disaster.
|
No Incident Response Plan
Being caught unprepared when Mordor inevitably attacks. Spoiler: they always do.
|
OPTEL maintains strict access controls, encryption, monitoring, and change management, essentially running a digital Helm’s Deep that’s always ready for battle.
Bottom line: Our softwares (VerifyBrand and Optchain) don’t just promise to protect customer data. We prove it, every single day.